Publications
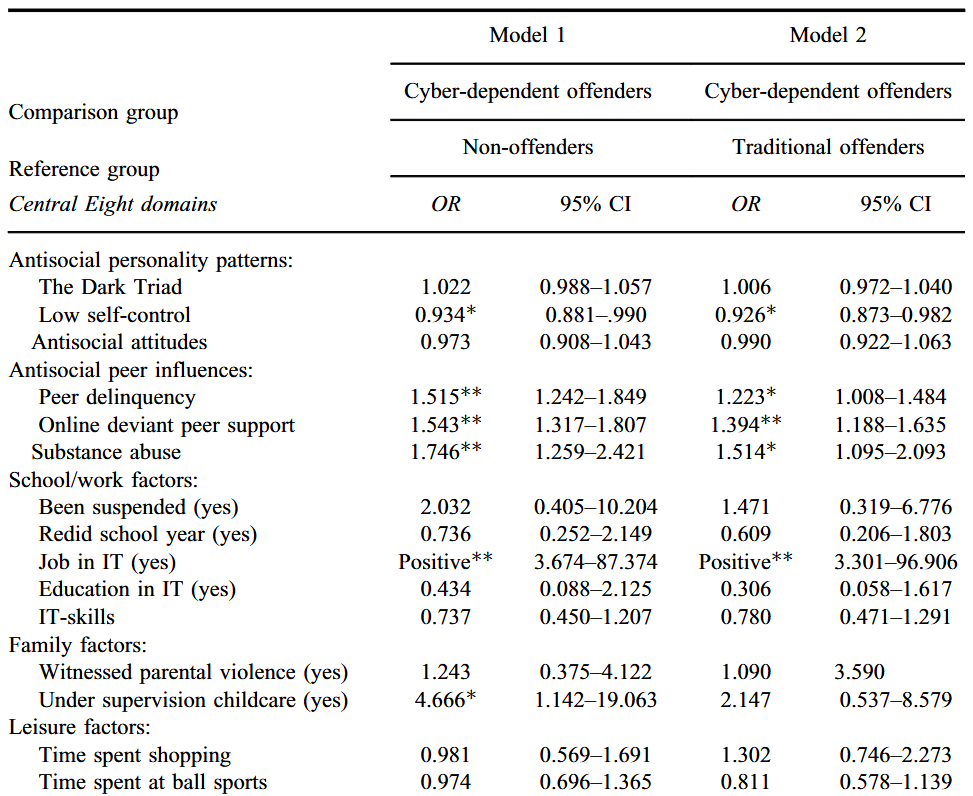
Distinct group, distinct traits? A comparison of risk factors across cybercrime offenders, traditional offenders and non-offenders
Journal article
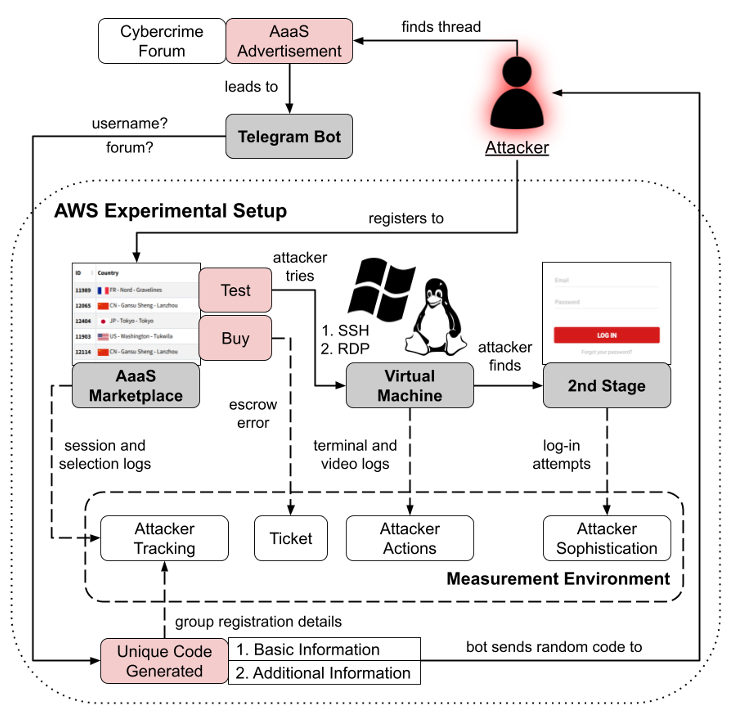
An Experimental Design to Investigate Attacker Actions on an Access-as-a-Service 'Criminal' Platform
Conference proceeding
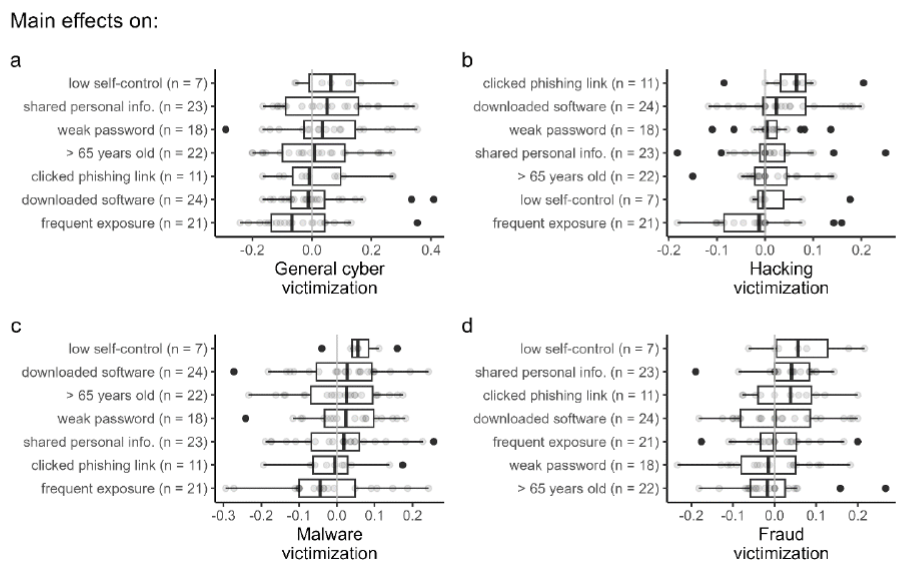
Risk Profiles for Cybercrime Victimization: A Conjunctive Analysis of Case Configurations
Journal article
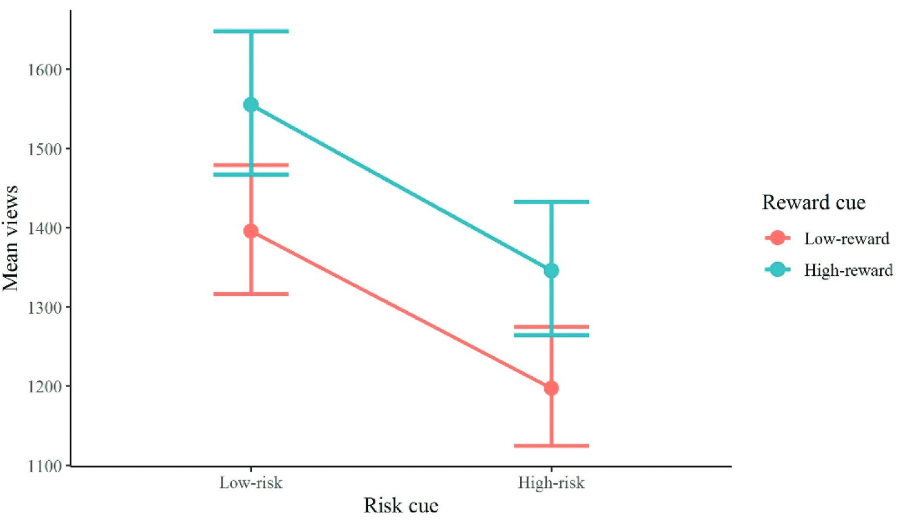
Rational choice on a hacker forum: The effect of risk and reward cues on target selection for account hijacking
Journal article
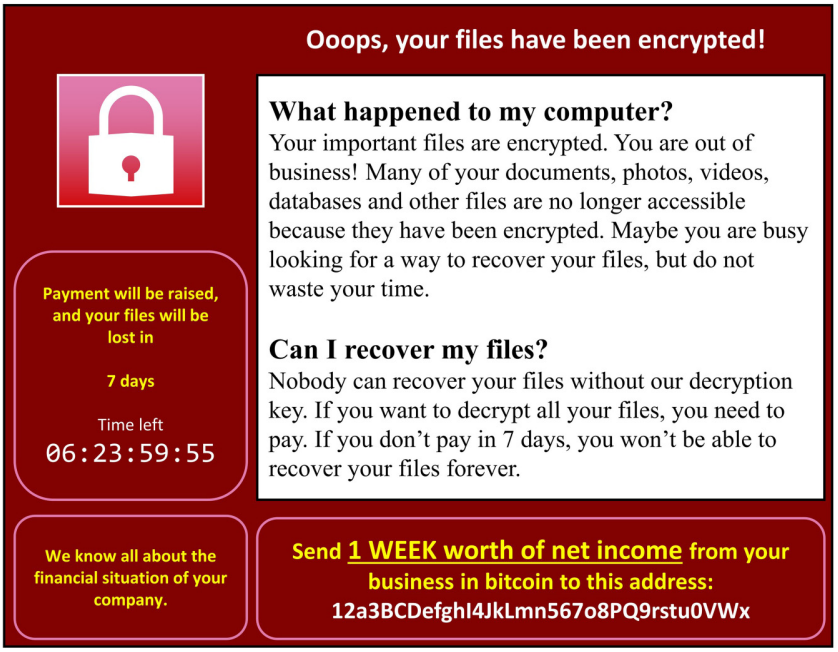
Examining ransomware payment decision-making among small- and medium-sized enterprises
Journal article
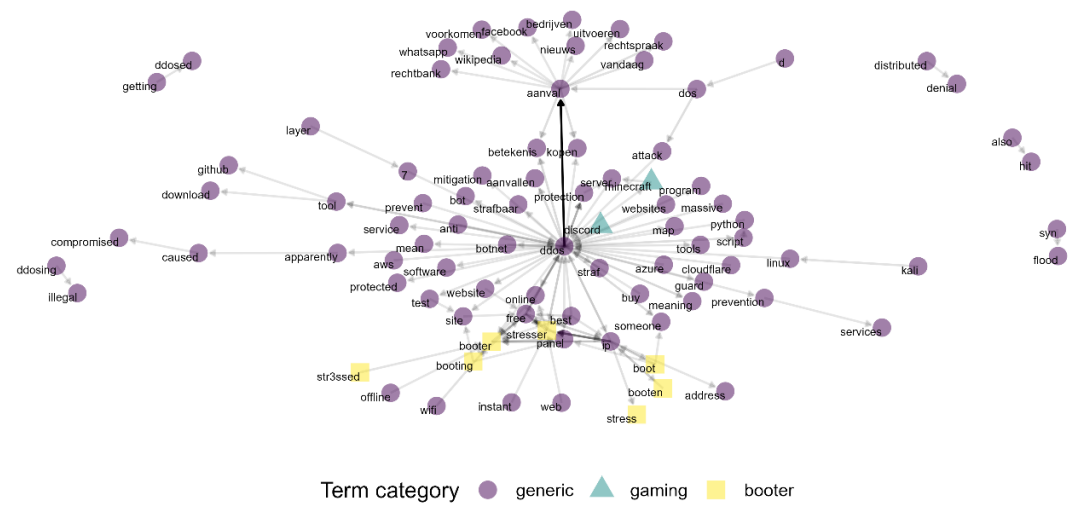
Interest in booter services and distributed denial of service attacks: Insight from Google search data
Journal article
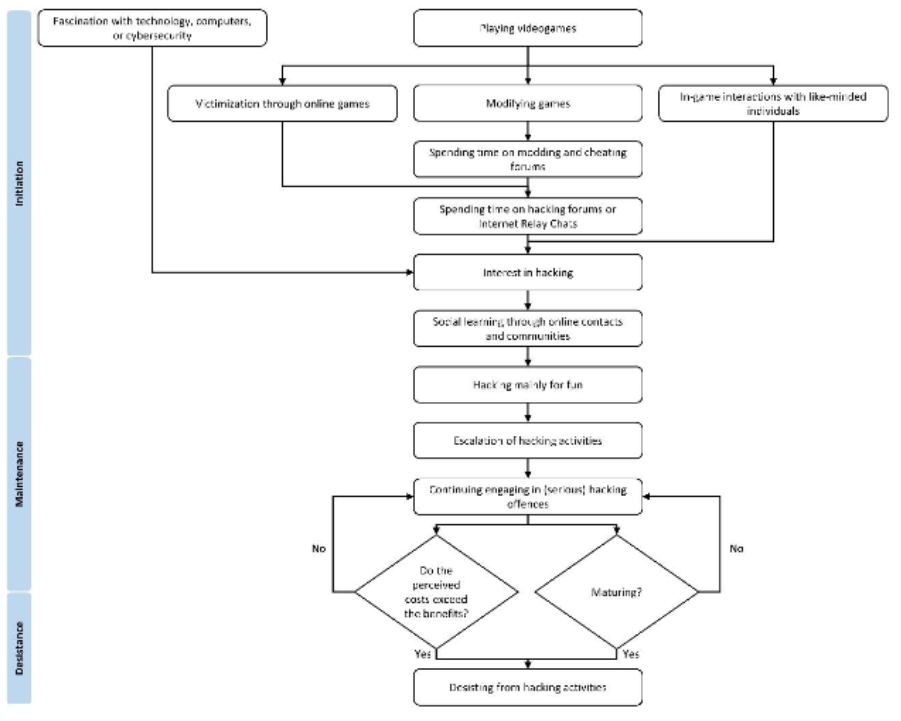
Pathways into, desistance from, and risk factors related to cyber-dependent crime: a systematic narrative review
Journal article
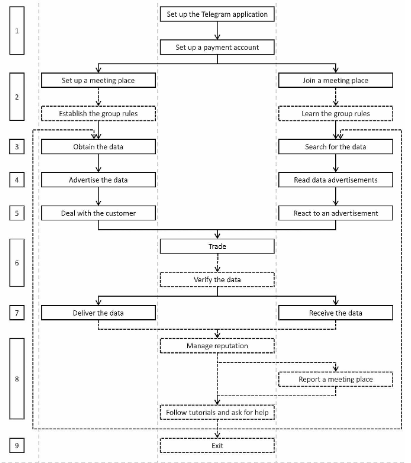
Stolen data markets on Telegram: a crime script analysis and situational crime prevention measures
Journal article
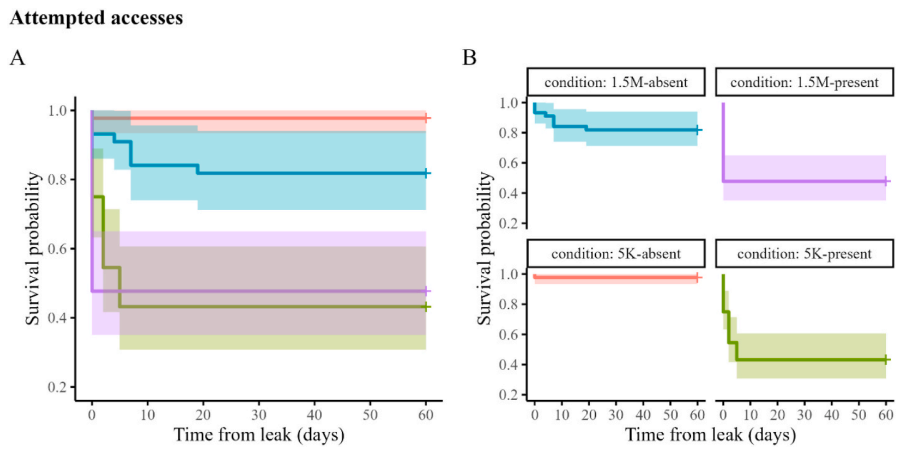
Sweeter than honey: Are Gmail accounts associated with greater rewards at a higher risk of hijacking?
Journal article
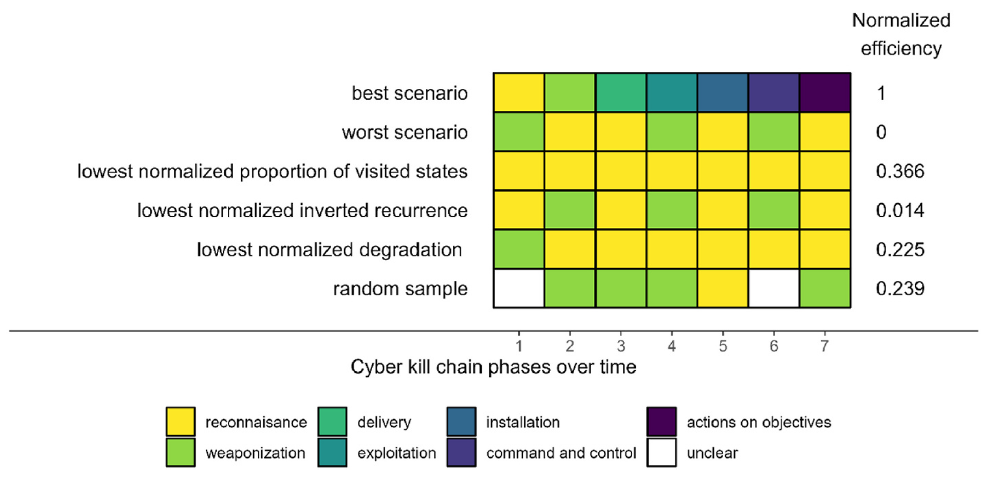
Criminal expertise and hacking efficiency
Journal article
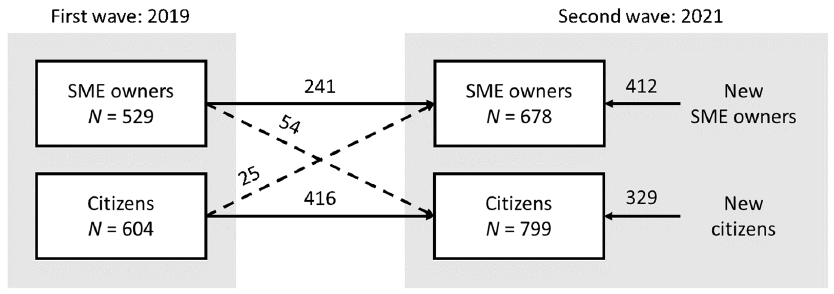
Cybercrime during the COVID-19 pandemic: Prevalence, nature and impact of cybercrime for citizens and SME owners in the Netherlands
Journal article
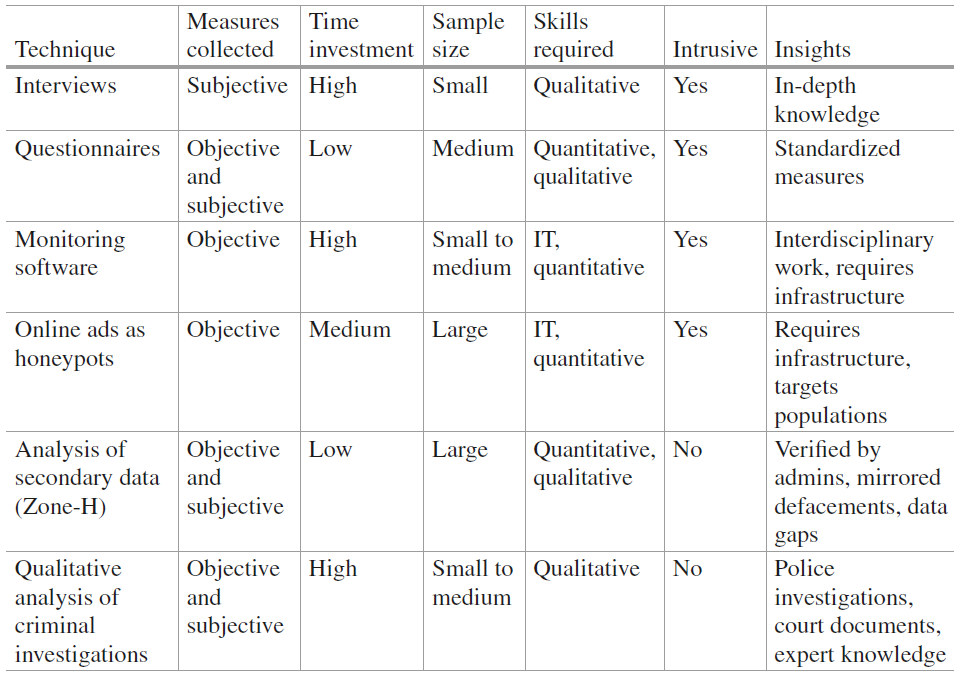
Fieldwork Experiences Researching Cybercriminals
Book chapter
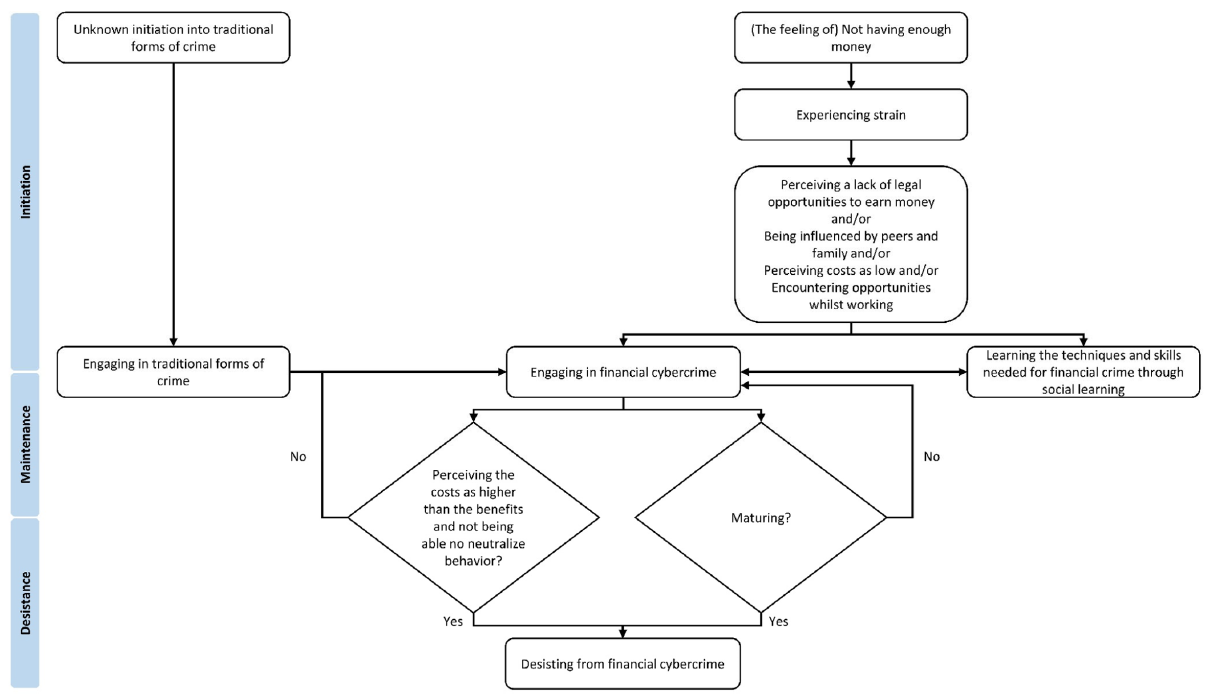
A systematic narrative review of pathways into, desistance from, and risk factors of financial-economic cyber-enabled crime
Journal article
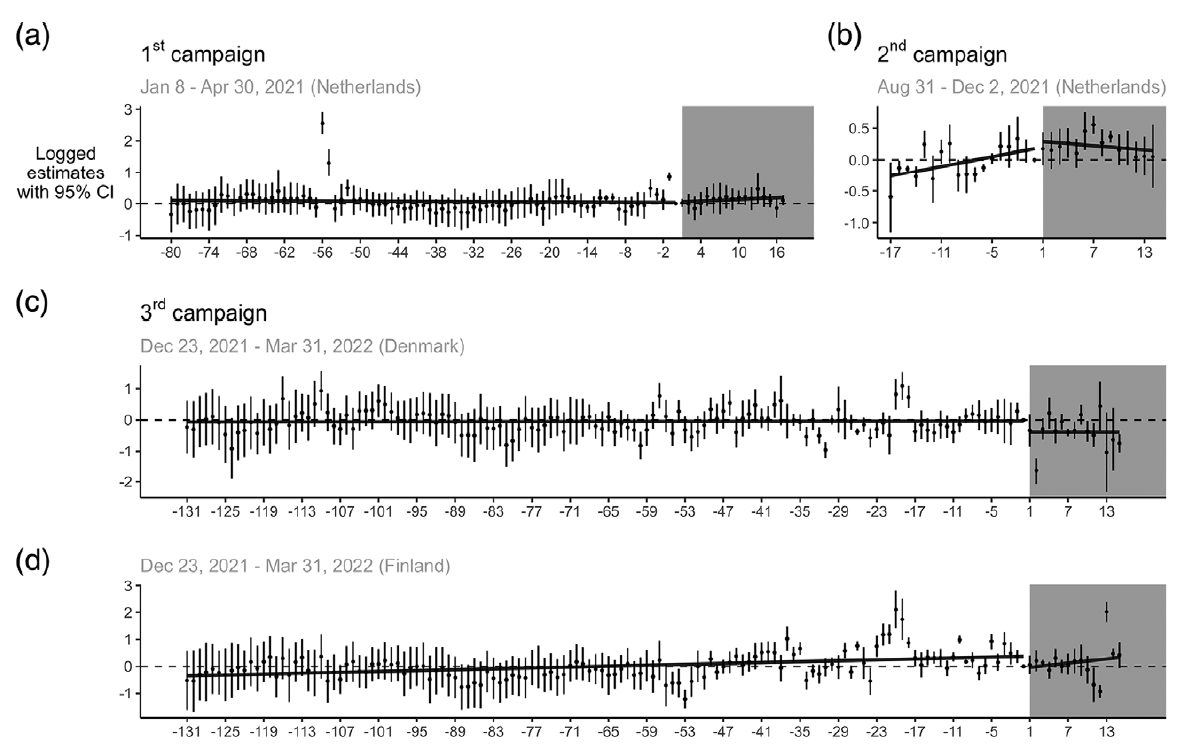
The effect of online ad campaigns on DDoS-attacks: A cross-national difference-in-differences quasi-experiment
Journal article
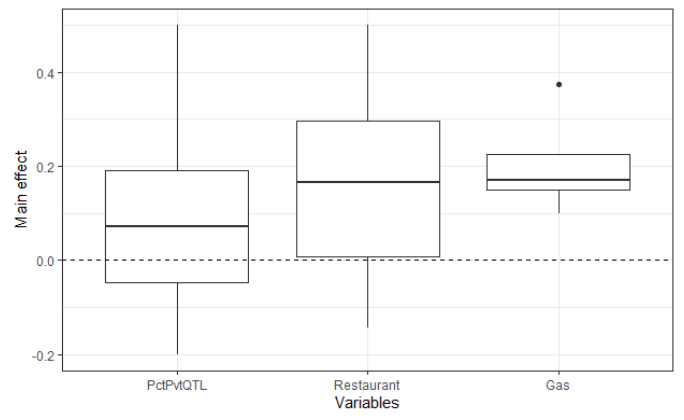
Conjunctive Analysis of Case Configurations (CACC)
Book chapter
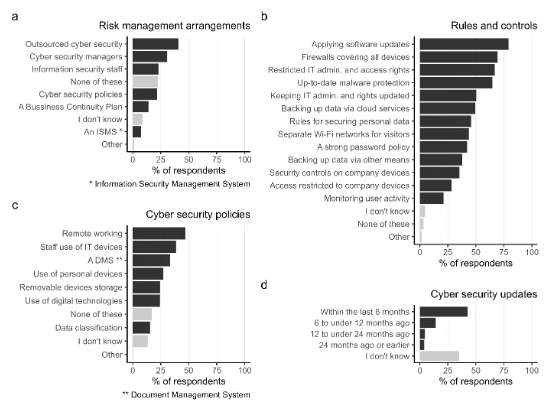
Insider threats among Dutch SMEs: Nature and extent of incidents, and cyber security measures
Journal article
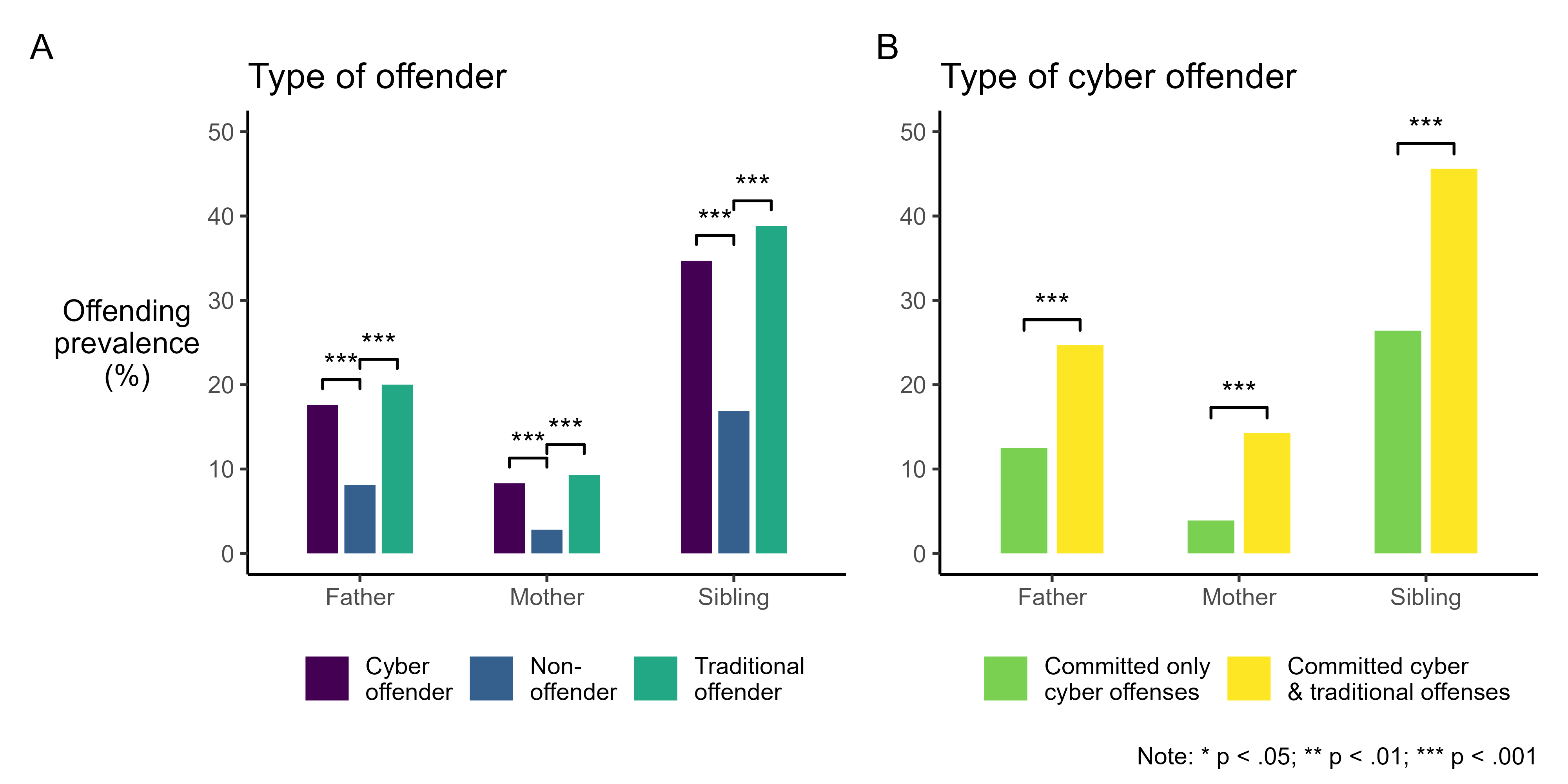
Familial concentration of crime in a digital era: Criminal behavior among family members of cyber offenders
Journal article
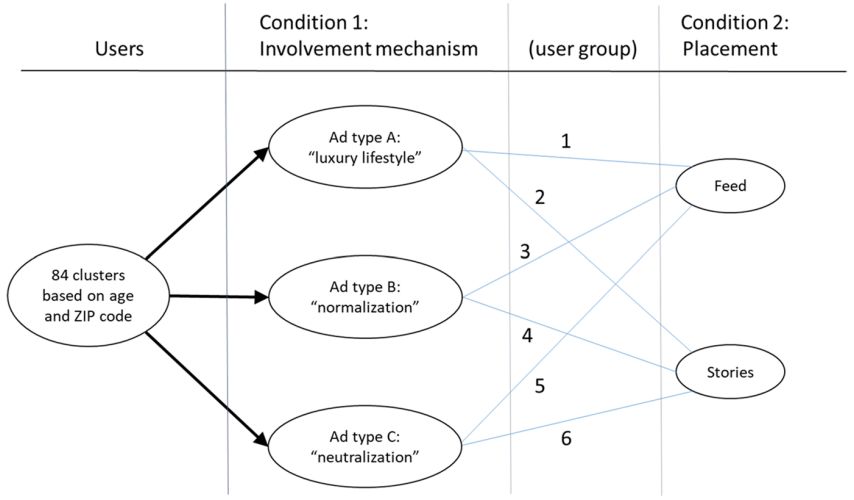
Understanding cybercrime involvement: a quasi-experiment on engagement with money mule recruitment ads on Instagram
Journal article
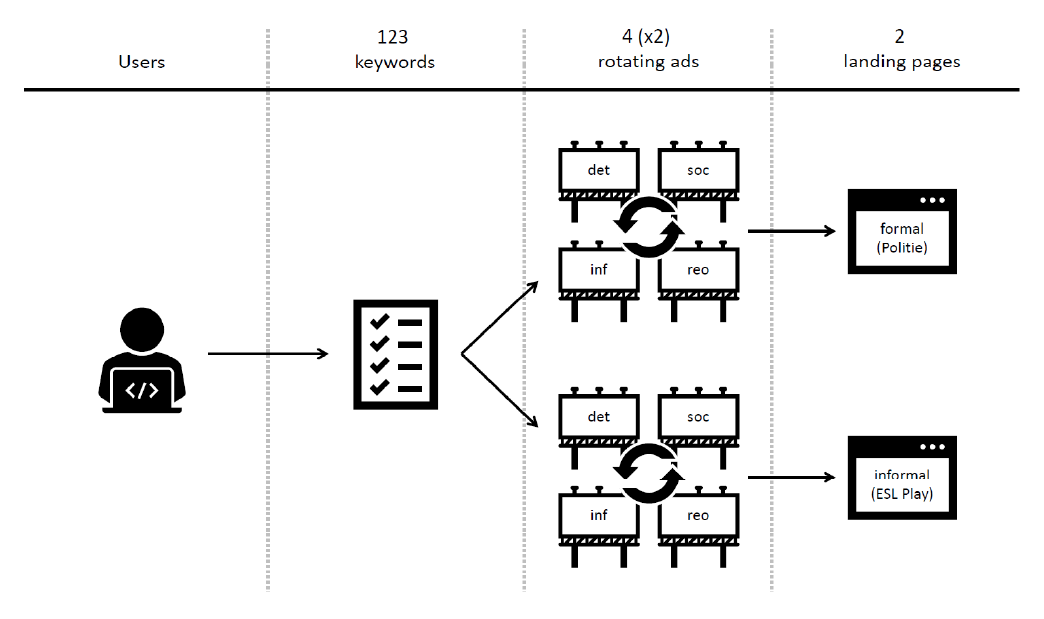
Alerting consciences to reduce cybercrime: A quasi-experimental design using warning banners
Journal article
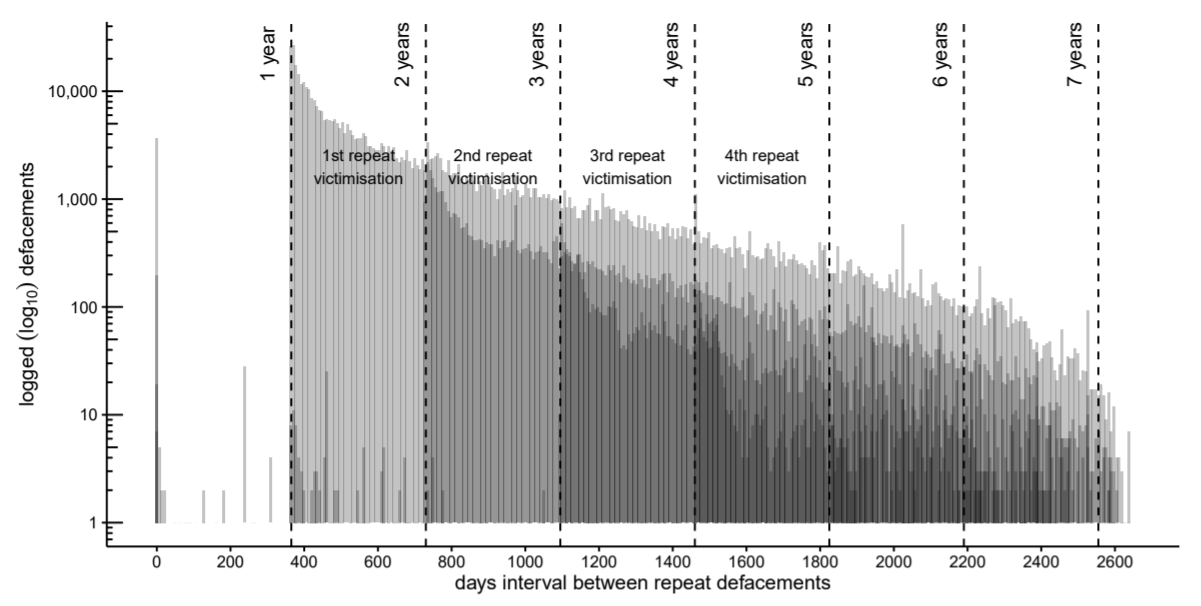
Repeat victimization by website defacement: An empirical test of premises from an environmental criminology perspective
Journal article
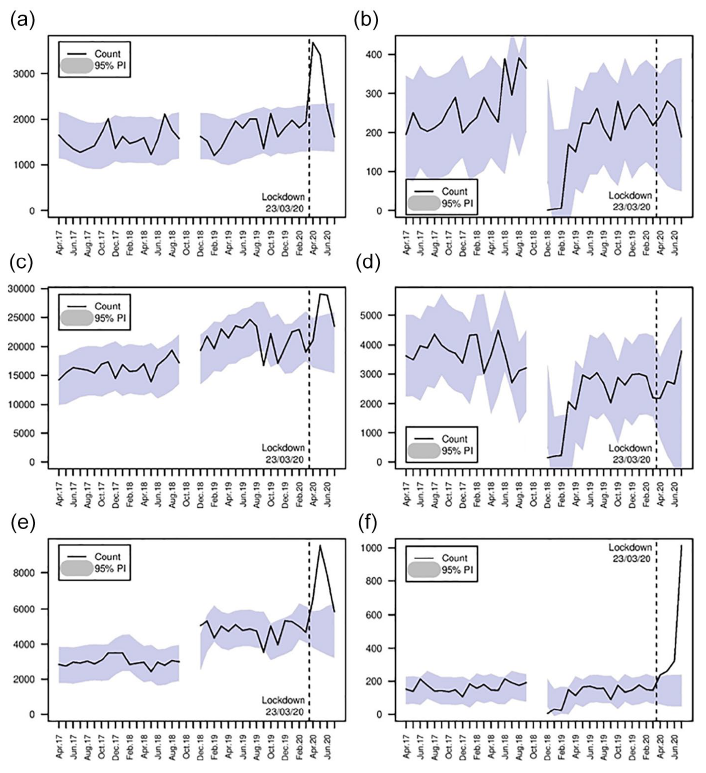
Empty streets, busy internet: A time-series analysis of cybercrime and fraud trends during COVID-19
Journal article
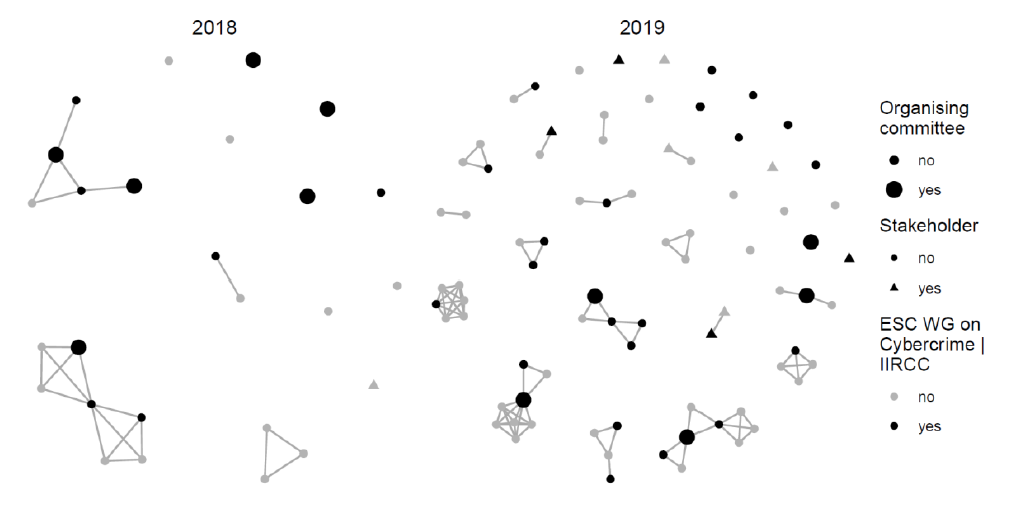
The Annual Conference on the Human Factor in Cybercrime: An analysis of participation in the 2018 and 2019 meetings
Book chapter
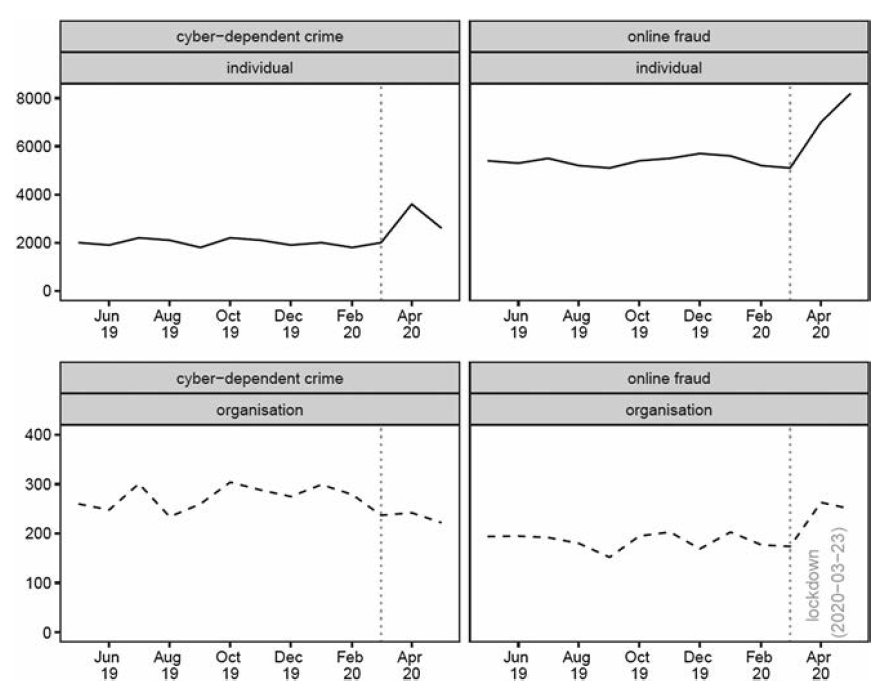
Cybercrime and shifts in opportunities during COVID-19: A preliminary analysis in the UK
Journal article
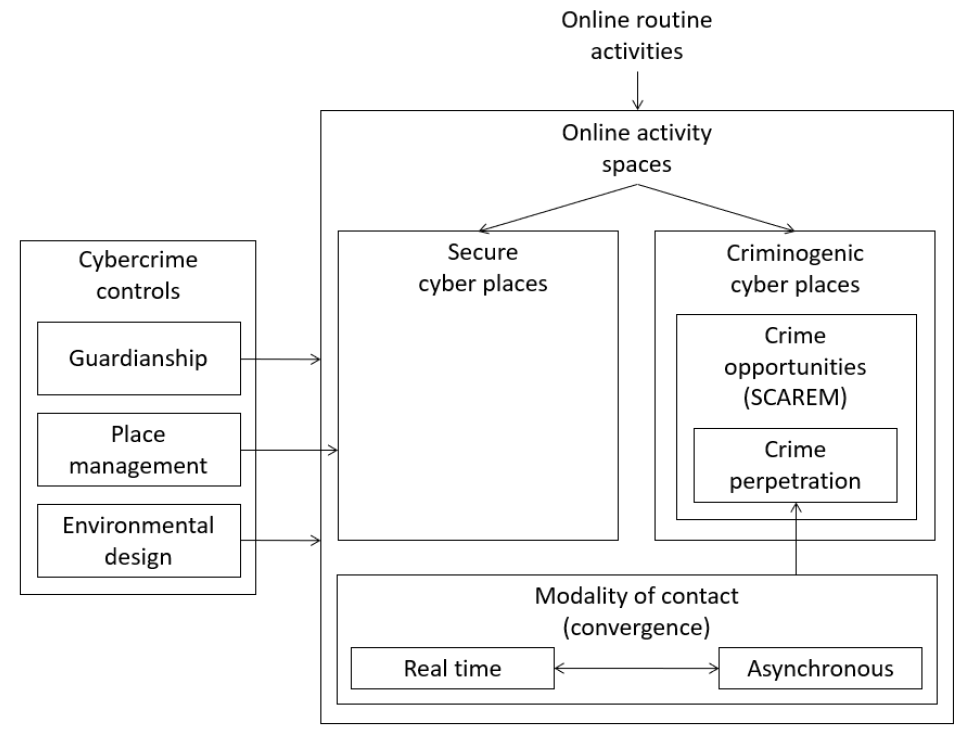
Cyber places, crime patterns, and cybercrime prevention: An environmental criminology and crime analysis approach through data science
Doctoral thesis

Environmental criminology and cybercrime: Shifting focus from the wine to the bottles
Book chapter

Hunter or prey? Exploring the situational profiles that define repeated online harassment victims and offenders
Journal article
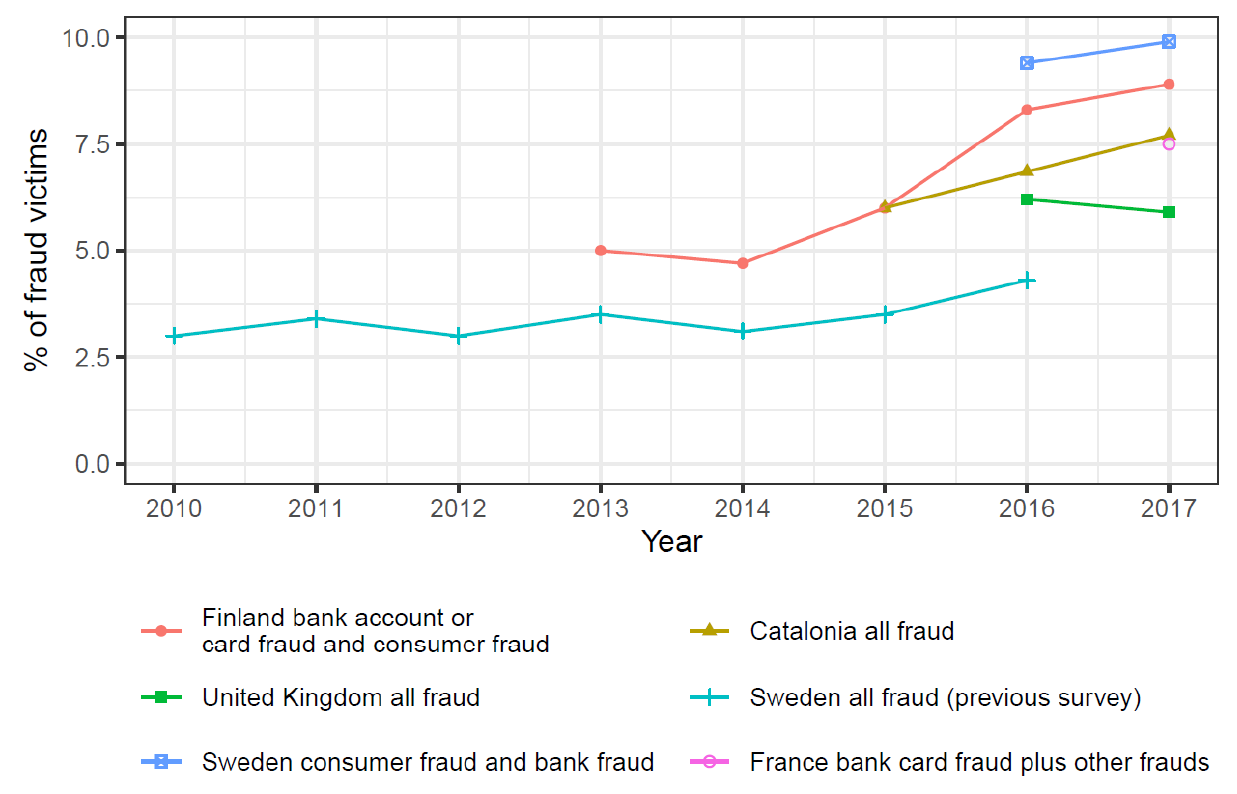
The dark figure and the cyber fraud Rise in Europe: Evidence from Spain
Journal article
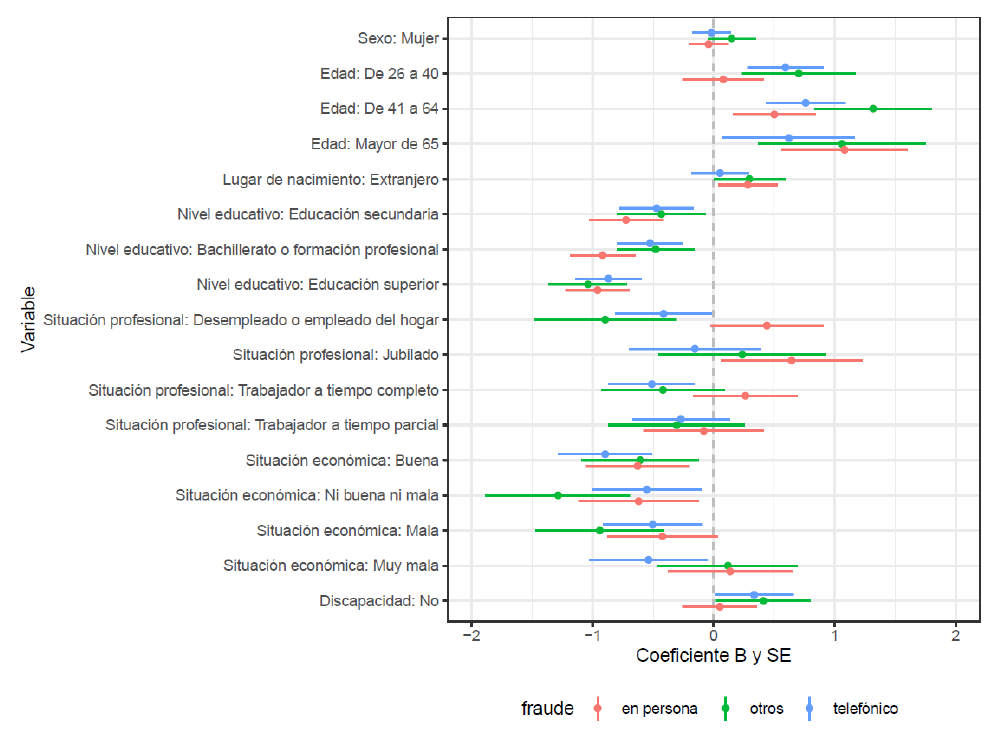
Comparing correlates of offline and online fraud victimisation and impacts
Journal article
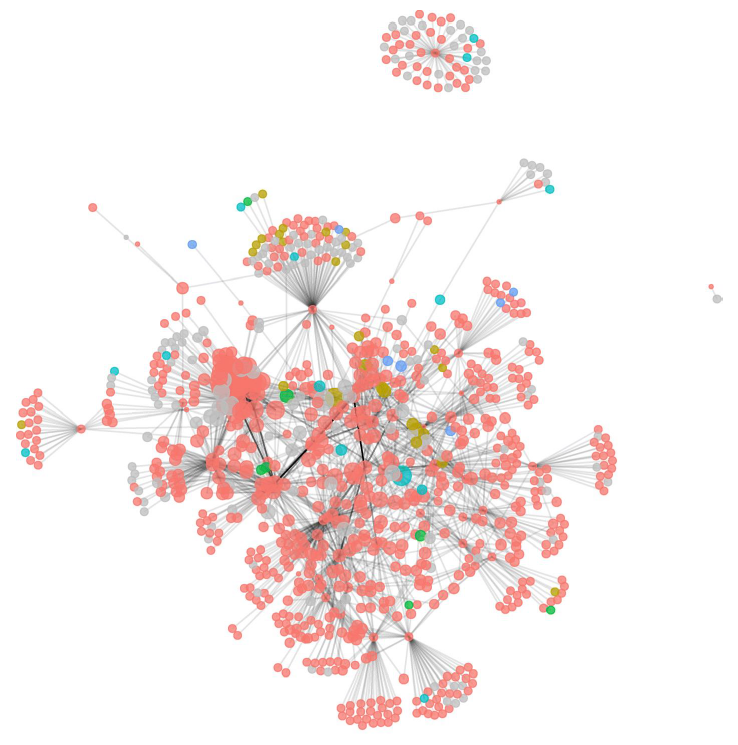
100% sure bets? Exploring the precipitation-control strategies of fixed-match informing websites and the environmental features of their networks
Journal article
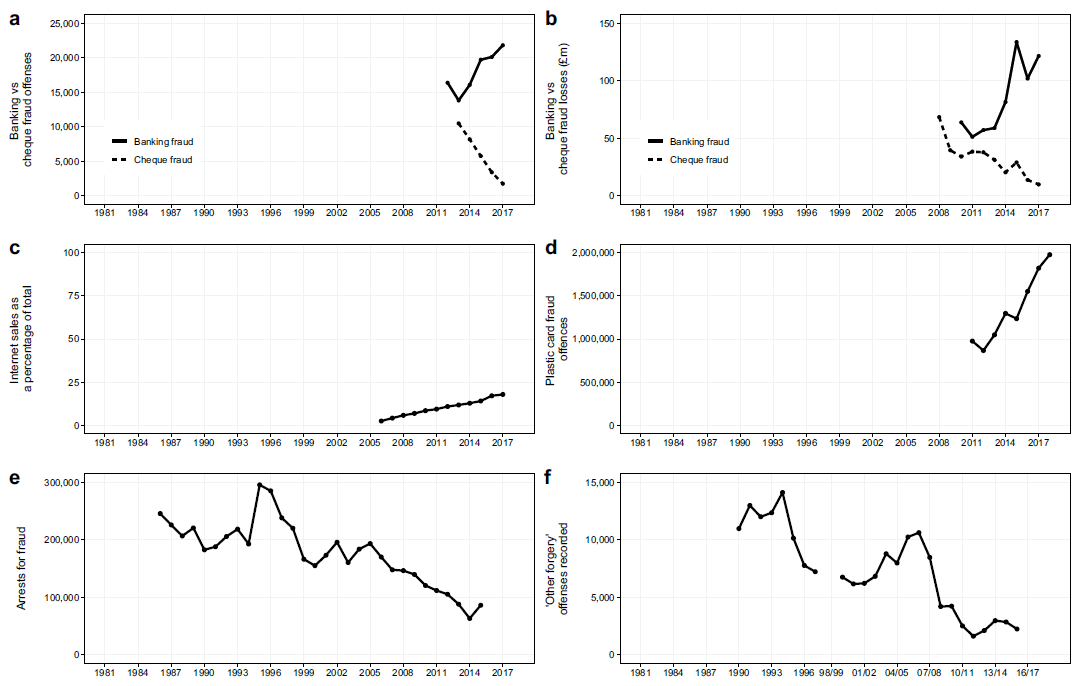
What about cyberspace (and cybercrime alongside it)? A reply to Farrell and Birks “Did cybercrime cause the crime drop?”
Journal article
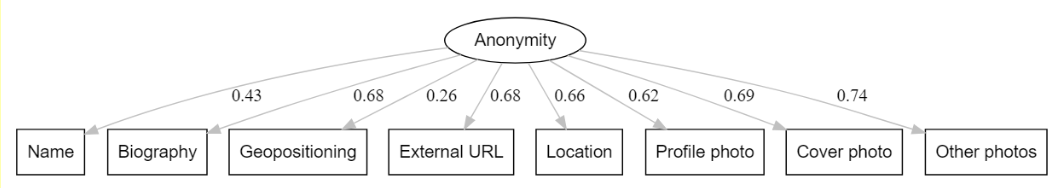
Can metadata be used to measure the anonymity of Twitter users? Results of a confirmatory factor analysis
Journal article
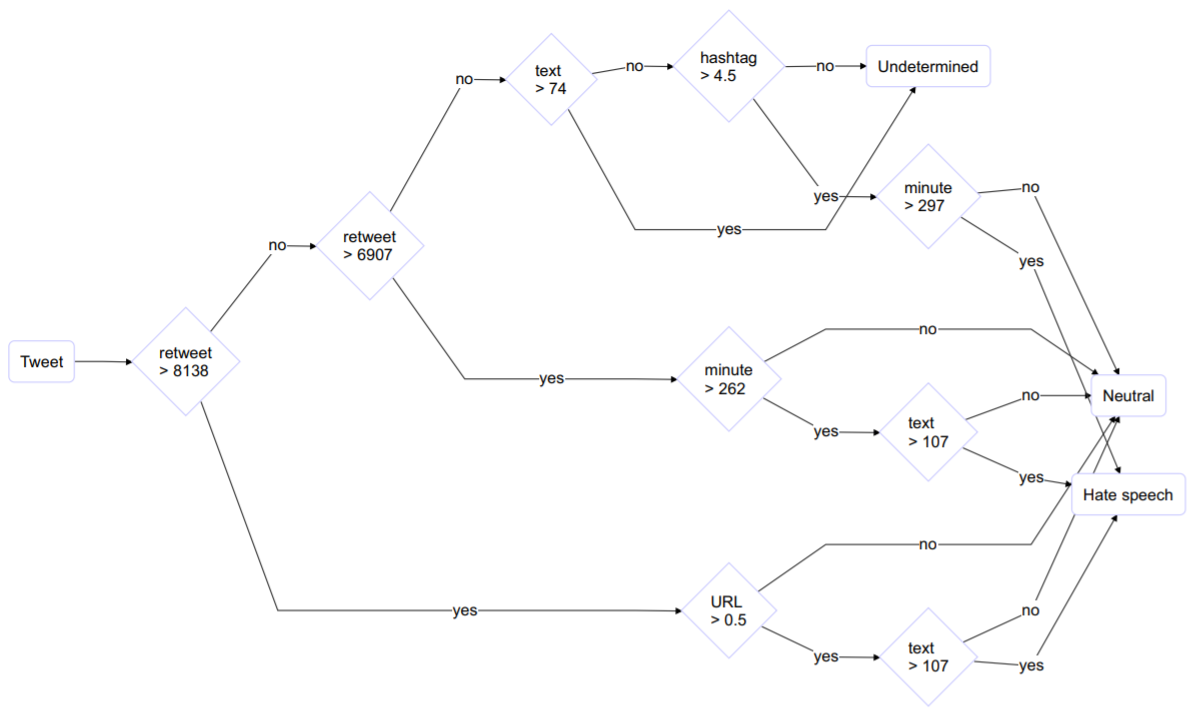
Hate is in the air! But where? Introducing an algorithm to detect hate speech in digital microenvironments
Journal article
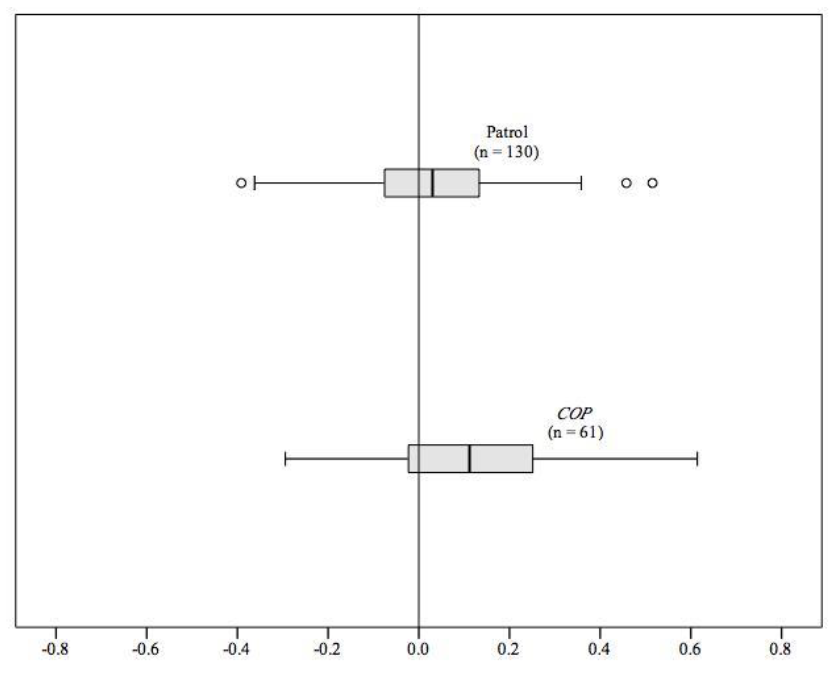
Conjunctive analysis of case configurations: An introduction to configural thinking
Journal article